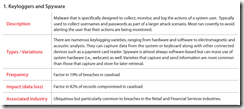
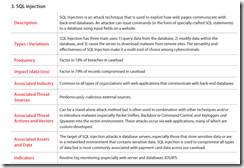
Instead of my usual "blogging frenzy" machine gun blast of short posts, I will just combine them into my new blog series "Fun Reading on Security AND Compliance." Here is an issue #22, dated December 29, 2009 (read past ones here) with which I flush my 2009 “2blog” folder clean :-)
This edition of dedicated to all of us who changed something in their lives in 2009.
- First, if you have to read only one thing, read everybody's security predictions for 2010: http://delicious.com/anton18/security+predictions+2010
- BTW, Ivan Arce touches on security in the year 2030 (!) here in this piece: “By 2030 an organization’s or individual’s information security risk posture will be better described as a probable trajectory in an global multi-dimensional risk landscape constantly evolving and the tools used to measure and manage risk will be built using the foundations of modern physics, evolutionary biology, economic modeling and social sciences rather than technology-dependent abstractions.”
- “What Information System Auditors and Information Security Auditors Do Not Want You To Know” is worth a read and my fave bit is: “…the future of the security profession will be deep and narrow technical knowledge. The generalist that walks around spouting best practices and reviewing documentation only will very quickly become a relic.”
- Gunnar promises that 2010 will be the year of “war on risk” in “2010 Goal #1: No more "general risk.” Quote: “Goal 1. Exorcise the word "risk" from the infosec profession, unless its qualified with an adjective.” This paper is an interesting one to read next as well.
- An interesting post that insinuates that Cisco is “exiting security market” (well, not really): “Cisco seems much more passive and confused about its security play then it did a few years ago when it seemed intent on owning all-things security.” While there, read this bit on Life and Death of Cisco MARS, their “once-mighty” (well, not really :-)) SIEM product. The feeding frenzy on the MARS corpse has already begun, with many vendors promising “drop-in MARS replacement” (not hard, given that so many MARS boxes were shelfware …mmm… ”shelf-appliances”)
- Fairly intelligent piece on choosing a SIEM from “CSO” magazine. Keep in mind that it is written by a journalist, so it has some inherent hilarity (such as 63,000:1 “compression”). BTW, CSO has another great piece: the first is a must read for all in security: “Lifestyle Hackers” – “The most interesting and ironic aspect of the lifestyle hacker is that he is motivated by the pursuit of productivity, often the very same motivation driving the implementation of various corporate controls”
- Melissa Hathaway comes out of the woodwork with her “Five Myths About Cybersecurity” and they are actually a great read, even if sort of obvious to security industry insiders.
- Ed Felten on “worst practices”, one of my favorite concepts: “A ‘Worst Practice’ is something that most of us do, even though we know it's a bad idea.[…] There's typically some kind of collective action problem that sustains a Worst Practice, some kind of Gordian Knot that must be cut before we can eliminate the practice.”
- And some more log reading, calling to love log analysis. And here as well, but more on the fuzzy size :-)
- While we are on the subject, Cisco published a great guide to logging: “Building Scalable Syslog Management Solutions” (which, BTW, never once mentions MARS – please forget MARS already). It event has a good discussion of “actionable vs. non-actionable syslogs” and some useful architecture bits.
- “PoS-gate” (a lawsuit from a merchant against 0wned Point of Sale system dealer and vendor Radiant Systems is covered: here, here, here, here and full suit here [PDF].
- Some fun DLP discussion here. In fact, In didn’t even know that DLP stands for “Disturbing Lack of Progress” :-) This seem to follow the same theme of “DLP skepticism” – also check the discussion afterwards.
- Very interesting philosophical piece by Rocky DeStefano on FUDSec: “We need to get out of the mindset of applying protection techniques based on physical realms and focus on evolving the entire environment to better suit our needs moving forward.” Some discussion of the above piece also continues here and here. While on FUDSec, check this awesome piece on utilities by Nick Selby; it is very useful if your paranoia is somehow losing its zing at the end of the year :-) (then read his other piece here too)
- A good read from Rich Mogul “The Anonymization of Losses: A Market Forces Failure”: “Losses are also anonymized on the corporate side. When an organization suffers a data breach, does the business unit involved suffer any losses? Do they pay for the remediation out of their departmental budget? Not in any company I've ever worked with -- the losses are absorbed by IT/security.” A very useful read to those who like to whine about security not being taken seriously (while compliance is)
- I just discovered that SANS is running their annual log management survey. It beats me why they are keeping it secret :-(
- Finally, I saved the most though provoking piece for last: this by Greg Hoglund paints a picture that few people even want to admit: “The decade in review: The most painful thing we learned is that computer security hasn’t worked. […] As we close out the first decade, we must realize we have just entered one of the biggest arms races in the history of warfare.”
PCI DSS section:
- A paper “Data Breaches Show PCI DSS Ineffective” can’t be good, can it? Well, this one actually is a good “incite-ful” read: “If PCI is a failure, it is not because it doesn’t prevent credit card theft; there is no such animal as a perfect set of countermeasures. PCI is a failure because it does not force a business to use it’s common sense and ask these practical, common-sense business questions.” In other words, it does not magically imbue the bearer with common sense :-)
- Other people are also thinking about using PCI DSS guidelines for protecting other data. The actual story from McAfee blog mentions some [idiot] organization that lost critical data that was not protected by “PCI-grade” safeguard.
- Another useful (=non-rant-ish) PCI DSS piece that I forgot to highlight: “Lessons Learned From PCI Compliance”
Enjoy!
Possibly related posts:
- All other security reading posts.
- All security predictions.