This is the analysis of my last poll; the responses are here and also below.
First, the most obvious conclusion: people still don't care much about log security; I am saying that since this was BY FAR the least popular of my polls. Only 24 people responded, so everything below is pretty unscientific :-) A good way to explain it: look at the recent media? Do these people care about their key business data and their customer data security? Nope. So, how on Earth do you make them care about securing their log data?
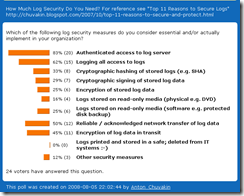
Second, it is entirely unsurprising that 83% of respondents want "Authenticated access to log server." In fact, I'd opine that 100% of people want authenticated access to any of their servers :-) But, this was my "red herring" to set the baselines for the rest of the questions...
However, this is where the buck stops: other security measures are notably less popular.
Third, "Logging all access to logs" is my favorite and I am happy to see it reported as popular. But do you really do it? Do you log access to log server OR access to actual logs? Think about it... I think a lot of people who do the latter still answered "yes" to this one.
Fourth, "Reliable / acknowledged network transfer of log data" and "Encryption of log data in transit " are two true "no-brainer" security features; they took the next spot at 45% and 50% of those who answered. They are simple, they are easy, they make sense - and, obviously, they don't make logs entirely secure so you need to do more. Why only 50%? Where is THE OTHER 50%?!
Fifth, "all things crypto" are below 40%. "Cryptographic hashing of stored logs", "Cryptographic signing of stored log data" and "Encryption of stored log data" all hover at around 30%. I attribute them to general disregard of log security AND reliance on "system security" (separate server, etc) over "data security" measures for log protection.
Finally, I am embarrassed to say that I missed the obvious security measure "Separate server for logging, not accessible from the Internet;" one of my readers added this using "Other security measures" choice. Indeed, this is a good point - and a good idea to do it. Another option mention there was "Destroy old logs." Amen to that too!
Possibly related posts:

2 comments:
Logs should be secured. But how?
Please don't tell me to buy a 6-digit logging appliance.
We bought a SEM and it SUCKS.
What now?
Securing logs sounds like a good idea. However, will this require the purchase of a 6-digit priced box? Hmmm. We bought a SEM and it sucks. We hate it. It doesn't work. Management is wary of log products. What now?
Post a Comment