Following the new "tradition" of posting a security tip of the week (mentioned here, here ; SANS jumped in as well), I decided to follow along and join the initiative. One of the bloggers called it "pay it forward" to the community.
So, Anton Security Tip of the Day #15: Fear and Loathing in Event 567
This tip digs into a seemingly simple, but really VERY esoteric subject: monitoring file access and modification via a Windows event log. Now, some people - who never studied this subject - tend to have a very simplistic view of this: just enable Object Access auditing, then right-click on a file or directory, click Security->Advanced->Auditing and then pick what types of events will be logged and by what accessing entities (i.e. users or computers). OK, so this will produce some logs, that is for sure. But are they useful?
First, why are we doing this? We typically need to know the following when we audit file access in Windows (or any other OS for that matter) for security (monitoring and investigation) or compliance:
- Time/date
- Computer where it happened
- User who touched the file
- Application he used to access the file
- File name + location (directory, share, etc)
- Type of access (read, write, create, delete, etc)
- Status (i.e. success or failure)
Can we get this from the above logs? No.
What? No!?! Really?
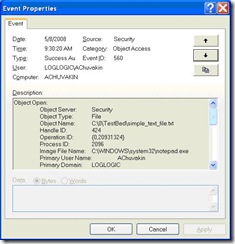
Yes, really. We can get some of the above, some of the time, not all of the above, all of the time. Here is an example, we are looking at event ID 560 (picture) and then at an extract from its description field.
Event:
Description (selected field):
Object Server: Security
Object Type: File
Object Name: C:\0\TestBed\simple_text_file.txt
Image File Name: C:\WINDOWS\system32\notepad.exe
Primary User Name: Anton
Primary Domain: XXXXXX
Accesses: READ_CONTROL
SYNCHRONIZE
ReadData (or ListDirectory)
WriteData (or AddFile)
AppendData (or AddSubdirectory or CreatePipeInstance)
ReadEA
WriteEA
ReadAttributes
WriteAttributes
WTH is that? Well, we know that the user 'Anton' has successfully read? wrote? changed attributes? did something? with a file named "C:\0\TestBed\simple_text_file.txt" using a program named "C:\WINDOWS\system32\notepad.exe." That's the best we can get, in this case! We may try to look at event IDs 562 and 567, but this missing information (i.e. the exact action performed) will not be added.
BTW, there will be a few more dozen (sometime hundreds!) of the 560s, 562s and 567s produced - all from just opening the text file in a notepad. The above event is notable for having BOTH "notepad" and "simple_text_file.txt" in the same event; others will have either of the two.
Anything else gets in the way? Yes, lots! MS Office will write to all files, even just opened for reading (with no user modifications to the content whatsoever), which will screw up your log monitoring efforts. If the file is on a share, more information will be missing (e.g. username might be).
So, how to use Windows event logs for file access tracking?
- Enable logging (as described above)
- Pick events 560 (most useful) and 562, 567 (useful too)
- Look for fun filenames that might be touched by the users (have a list of files and users handy)
- Figure out what programs were used to access them (this is called "Image File Name" in "WinLogSpeak")
- Ponder the 'Accesses' section of each event until your brain turns blue :-) or until you decide whether such access is authorized or not...
Overall, this is still very useful for file access monitoring, but the process is paaaaaainful.
BTW, I am tagging all the tips on my del.icio.us feed. Here is the link: All Security Tips of the Day.

No comments:
Post a Comment