OMG, today is The Breach Day, an official security holiday. Verizon Business has just released their super-famous “2011 Data Breach Investigations Report”
Here are my notes, thoughts, jokes and highlights (are images and quotes are from VzDBIR 2011).
First, we all know that science has been looking for a scientific proof of stupidity for years, and finally it is here, delivered through the power of a Pie Chart below:

In other words, most of the damaging, expensive breaches has cheap countermeasures that people just don’t do. Niiiice!
On a more serious note, not only many of the breached organizations were ignorant, there were not even close to being PCI DSS compliant (more on this below).

Doesn’t it make you think that we are going backwards in security, “APT” notwithstanding?
So, who ARE these people? Well, we now know:

Key industries are those know for limited infosec resource and lots of juicy payment card numbers, often combined with other useful information such as mailing addresses.
That is likely why we have less records stolen overall (no known mega-breaches), but A LOT of smaller “losses”, largely attributes to industrial “hacking machine” of cybercrime hitting smaller business head-on.
And how exactly they are getting owned – surely with an ancient Chinese secret APT hacking tools? Well, yeah – on the “ancient” part”: it is password guessing mostly that harks back from the 1970s:

So, Verizon says: please go and change that password that still says "password" - you will help your security posture a lot!
What specific computing assets are bearing the brunt of attacks? This easy diagram shows:
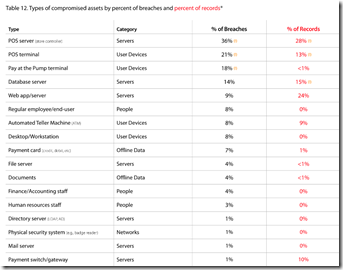
So, merchants, do you still have that POS server in the back of the store with PANs of all the cards you ever accepted? Congrats, your donation to cybercrime fund has been accepted…
To make things even sadder, people are not detecting shit:

The above shows that the most typical time between the incident and its detection is “weeks.” Still want to field that real-time monitoring system? Save some money and buy a cheaper log management system + establish a solid log review process (example).
The Verizon team does give the same advice I often give my clients today: "Change your approach to event monitoring and log analysis: Based on the data we collect in the Time of Breach events, we believe that organizations would be better served to focus less on the “real-time” methods of detection, and more on the “this week” methods. If we can shift Compromise to Discovery time frame from Weeks and Months to Days, it will significantly reduce the damage done to your organization"
Let’s REALLY crank up the sadness – even after WEEKS or MONTHS, who is actually doing detecting? Not the security team, mind you. Yup, The Third Party wins again!

Your own log review detects breaches LESS OFTEN then “happenstance discovery by unrelated 3rd party” [why? because you ain’t doing that log review!] So, random people stumbling on your weeks-old breach evidence is more "effective" than your log analysis. This is how bad things really are… The above graph made me cry in pain, BTW.
Specifically, the report states "If there is one positive note that we can squeeze out of these statistics around active measures, it’s that discovery through log analysis and review has dwindled down to 0%. So the good news is that things are only looking up from here. Yeah, that’s squeezing pretty hard, but what else can we do? Figure 41 continues to show that good evidence of the breach usually exists in the victim’s log files waiting to be used. "
Finally, does PCI compliance helps? Well, we’d know only if the organizations were in compliance, and most aren’t (not even at ASSESSMENT TIME, much less at BREACH TIME):

End of the story, really.
Overall, this was the saddest VzDBIRs I ever read … Wade and Alex, you made me and my puppy weep My highlights might be fun, but PLEASE do take time to read the entire report [PDF]!!
My highlights might be fun, but PLEASE do take time to read the entire report [PDF]!!
Possibly related posts:
Here are my notes, thoughts, jokes and highlights (are images and quotes are from VzDBIR 2011).
First, we all know that science has been looking for a scientific proof of stupidity for years, and finally it is here, delivered through the power of a Pie Chart below:

In other words, most of the damaging, expensive breaches has cheap countermeasures that people just don’t do. Niiiice!
On a more serious note, not only many of the breached organizations were ignorant, there were not even close to being PCI DSS compliant (more on this below).

Doesn’t it make you think that we are going backwards in security, “APT” notwithstanding?
So, who ARE these people? Well, we now know:

Key industries are those know for limited infosec resource and lots of juicy payment card numbers, often combined with other useful information such as mailing addresses.
That is likely why we have less records stolen overall (no known mega-breaches), but A LOT of smaller “losses”, largely attributes to industrial “hacking machine” of cybercrime hitting smaller business head-on.
And how exactly they are getting owned – surely with an ancient Chinese secret APT hacking tools? Well, yeah – on the “ancient” part”: it is password guessing mostly that harks back from the 1970s:

So, Verizon says: please go and change that password that still says "password" - you will help your security posture a lot!
What specific computing assets are bearing the brunt of attacks? This easy diagram shows:

So, merchants, do you still have that POS server in the back of the store with PANs of all the cards you ever accepted? Congrats, your donation to cybercrime fund has been accepted…
To make things even sadder, people are not detecting shit:

The above shows that the most typical time between the incident and its detection is “weeks.” Still want to field that real-time monitoring system? Save some money and buy a cheaper log management system + establish a solid log review process (example).
The Verizon team does give the same advice I often give my clients today: "Change your approach to event monitoring and log analysis: Based on the data we collect in the Time of Breach events, we believe that organizations would be better served to focus less on the “real-time” methods of detection, and more on the “this week” methods. If we can shift Compromise to Discovery time frame from Weeks and Months to Days, it will significantly reduce the damage done to your organization"
Let’s REALLY crank up the sadness – even after WEEKS or MONTHS, who is actually doing detecting? Not the security team, mind you. Yup, The Third Party wins again!

Your own log review detects breaches LESS OFTEN then “happenstance discovery by unrelated 3rd party” [why? because you ain’t doing that log review!] So, random people stumbling on your weeks-old breach evidence is more "effective" than your log analysis. This is how bad things really are… The above graph made me cry in pain, BTW.
Specifically, the report states "If there is one positive note that we can squeeze out of these statistics around active measures, it’s that discovery through log analysis and review has dwindled down to 0%. So the good news is that things are only looking up from here. Yeah, that’s squeezing pretty hard, but what else can we do? Figure 41 continues to show that good evidence of the breach usually exists in the victim’s log files waiting to be used. "
Finally, does PCI compliance helps? Well, we’d know only if the organizations were in compliance, and most aren’t (not even at ASSESSMENT TIME, much less at BREACH TIME):

End of the story, really.
Overall, this was the saddest VzDBIRs I ever read … Wade and Alex, you made me and my puppy weep
Possibly related posts:
