Just a random piece of some research project I did at some random point :-) In discussions at RSA 2010 conference, somebody mentioned that SIEM, log management and other monitoring/detection security product users are split into two major categories: one actually uses the product while the other “buys it for compliance” and then eventually uses … as a doorstop, for example.
And I actually had an old presentation about this that was offered as strategic guidance to my consulting client (a vendor).
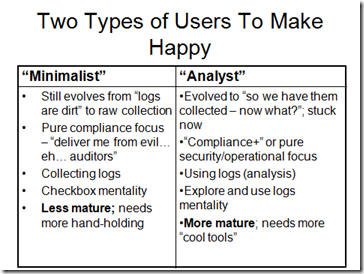
Here is that picture and text: two types of SIEM/log managements users that your solution has to make happy:
“Minimalist” SIEM/LM User
•Still evolves from “logs are dirt” to raw collection of log data
•Pure compliance focus – “deliver me from evil… eh… auditors” (or assessors, in case of PCI DSS)
•Collecting logs is the primary “activity”; not even thinking about log review yet
•Checkbox mentality is rampant among that type of user (sometimes, “correlation” is one of the checkboxes, sadly)
•Less mature; needs more hand-holding when deploying the product (might not want any help though…)
“Analyst” SIEM/LM User
•Evolved to “so we have them collected – now what?”; stuck now and not sure how to use “all that data”
•“Compliance+” or even pure security/operational focus; for example, SOC operation
•Using logs – review, analysis, at the very least investigations
•Explore and use logs mentality, focuses on getting the value of the data and solving problems
•More mature; needs more “cool tools”
So, before you plan/design/build your solution, think what is the primary user type… but keep in kind that to be truly successful you might need to entice both.
Enjoy!
Possibly related posts: