“2009 Data Breach Investigations - Supplemental Report: Anatomy of a Data Breach” is OUT! Grab it here or here at their blog.
Some highlights follow below:
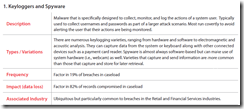
- This covers the use of keyloggers in investigated breach cases – note a high percentage of stolen records:
BTW, read the case study after this table – very insightful
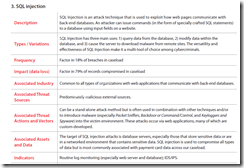
- This tells the same sad story, but about backdoors and bots – note a high percentage of records and the use of SQL injection:
Also, read the case study after this; it has gems like “as to how the assailants first gained access, investigators found a non-sanctioned commercial remote
desktop program on one of the R&D workstations [that handled super-secret ‘business-buster’ data].”
- The attack entry on SQL injection is event more fun – note the reference to database logs (“Routine log monitoring (especially web server and database)”):
- Other fun bits (the whole thing is one big bundle of fun though!) are: “Striving for perfection in any one control is inefficient and introduces single-point of failure dependencies” and “loose-grained access control applied to routers, firewalls, and other network devices are extremely efficient due to the large number of known and unknown problems they mitigate.” [please shove it to folks who proclaim ‘firewall is dead’] I also liked the VzBIR vs DataLossDB comparison in the appendix.
- Conclusion: Verizon report series exude pure awesomeness!
Do read the full supplemental report!
Possibly related posts: